Install Pi-hole on Raspberry Pi
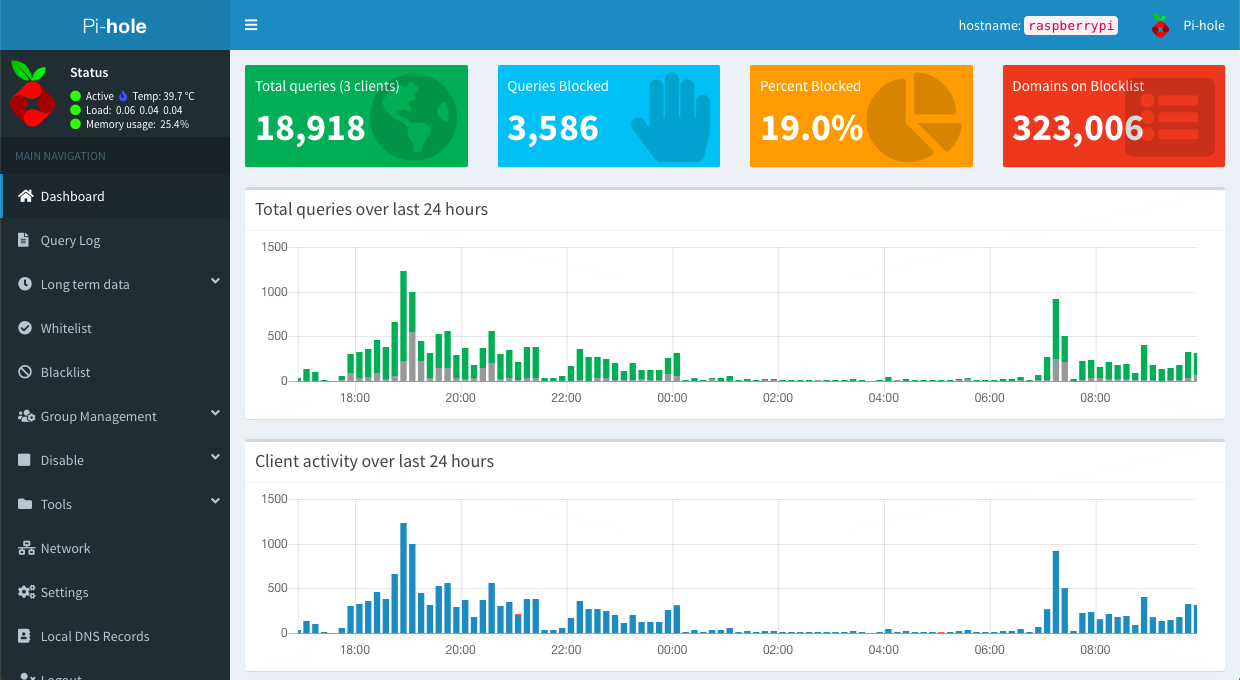
Pi-hole is a network-wide ad blocking system, it can be installed on any model of Raspberry Pi, in this blog post I’ll show you how to install it on 3A+, configure it and add some useful adlist.
Install Raspberry Pi OS
First thing need to do is download and install Raspberry Pi OS, get the latest image and write it to microSD card with balenaEtcher.
Setup Wireless Network
Because Raspberry Pi 3A+ does not have Ethernet support, so we need to configure WiFi before using it as a ad-blocker.
Create a file wpa_supplicant.conf under root of the boot partition with:
ctrl_interface=DIR=/var/run/wpa_supplicant GROUP=netdev
update_config=1
country=<Insert 2 letter ISO 3166-1 country code here>
network={
ssid="<Name of your wireless LAN>"
psk="<Password for your wireless LAN>"
}
Don’t forget to change the country code and WiFi credentials.
Enable SSH Access
In order to install Pi-hole, we need to remote access to the pi board, enable ssh
by creating a file named ssh in the same directory as wpa_supplicant.conf, the
content does not matter.
Install Pi-hole
With Raspberry Pi OS installed and ssh enabled, now lets get hands dirty.
Power up Pi board and find the IP address in the router, then then logon with:
# Default password is raspberry
ssh pi@192.168.1.111
Pi-hole installation is as easy as just with one command:
# Install Pi-hole
curl -sSL https://install.pi-hole.net | bash
And follow the directions to finish the installation.
You may need to add an entry to your host file, if you have problems accessing
raw.githubusercontent.com:
echo '151.101.56.133 raw.githubusercontent.com' >> /etc/hosts
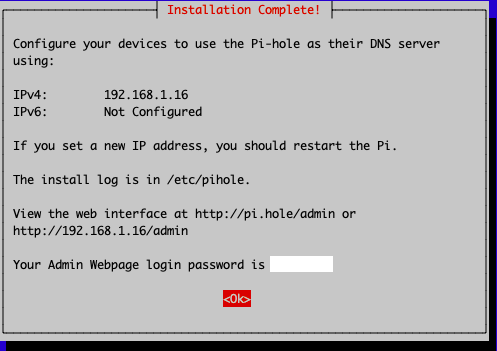
At the end of installation, you need to write down the login password:
Configure Home Router
The easiest way to use Pi-hole is to set your router’s DNS server to IP address of Pi-hole.
Manage Adlists
You may find you need to add more addlist to accommodate for you needs, you can
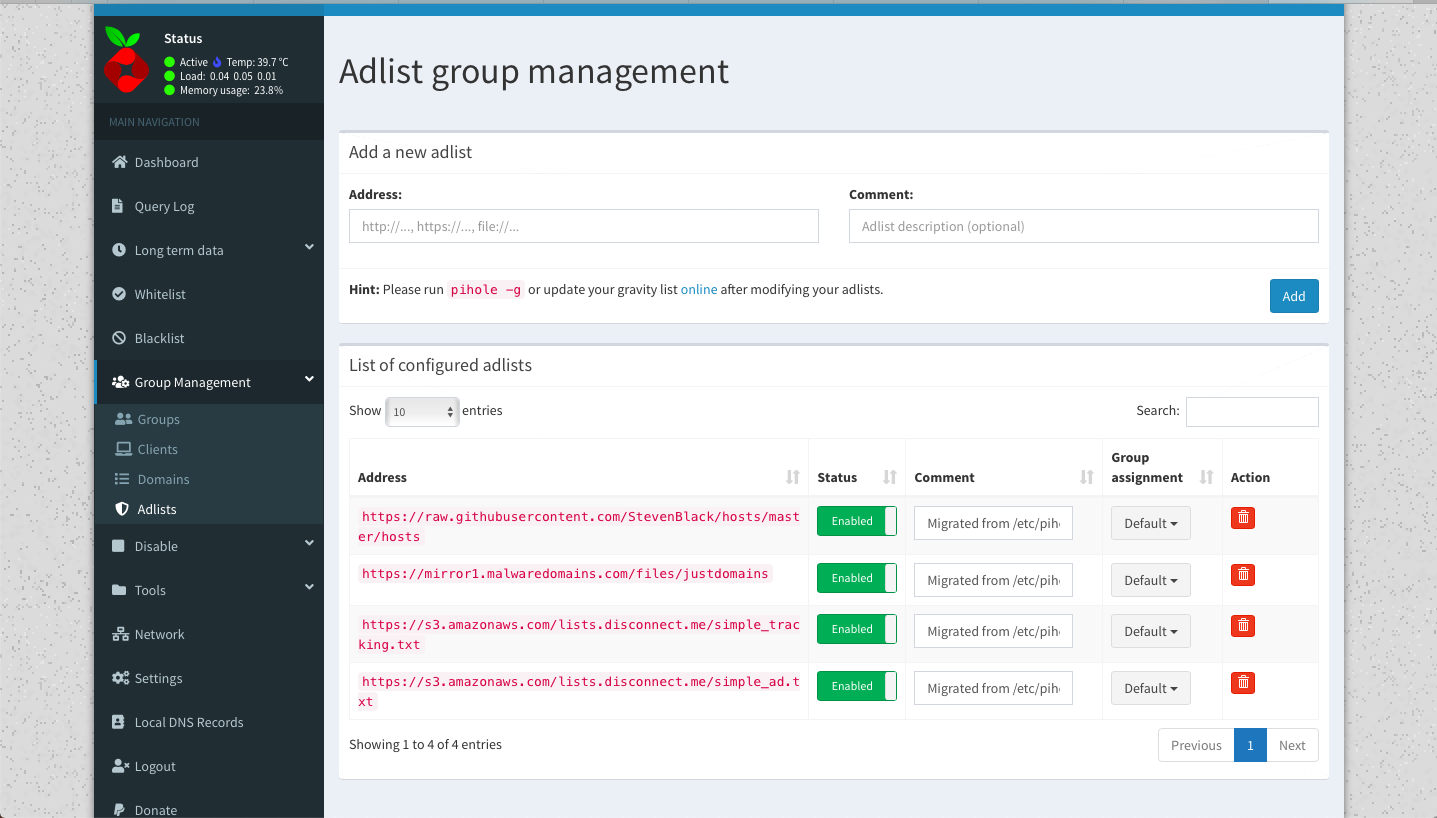
manage the Adlists using the Pi-hole web interface, with just few clicks,
go to Group Management >> Adlists copy the host URL to Address and click Add:
I added all the ticked rules found in The Firebog for ad blocking:
https://raw.githubusercontent.com/PolishFiltersTeam/KADhosts/master/KADhosts_without_controversies.txt
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.Spam/hosts
https://v.firebog.net/hosts/static/w3kbl.txt
https://adaway.org/hosts.txt
https://v.firebog.net/hosts/AdguardDNS.txt
https://v.firebog.net/hosts/Admiral.txt
https://raw.githubusercontent.com/anudeepND/blacklist/master/adservers.txt
https://v.firebog.net/hosts/Easylist.txt
https://pgl.yoyo.org/adservers/serverlist.php?hostformat=hosts&showintro=0&mimetype=plaintext
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/UncheckyAds/hosts
https://raw.githubusercontent.com/bigdargon/hostsVN/master/hosts
https://v.firebog.net/hosts/Easyprivacy.txt
https://v.firebog.net/hosts/Prigent-Ads.txt
https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-blocklist.txt
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.2o7Net/hosts
https://raw.githubusercontent.com/crazy-max/WindowsSpyBlocker/master/data/hosts/spy.txt
https://hostfiles.frogeye.fr/firstparty-trackers-hosts.txt
https://raw.githubusercontent.com/DandelionSprout/adfilt/master/Alternate%20versions%20Anti-Malware%20List/AntiMalwareHosts.txt
https://osint.digitalside.it/Threat-Intel/lists/latestdomains.txt
https://s3.amazonaws.com/lists.disconnect.me/simple_malvertising.txt
https://v.firebog.net/hosts/Prigent-Crypto.txt
https://v.firebog.net/hosts/Prigent-Malware.txt
https://mirror.cedia.org.ec/malwaredomains/immortal_domains.txt
https://www.malwaredomainlist.com/hostslist/hosts.txt
https://bitbucket.org/ethanr/dns-blacklists/raw/8575c9f96e5b4a1308f2f12394abd86d0927a4a0/bad_lists/Mandiant_APT1_Report_Appendix_D.txt
https://phishing.army/download/phishing_army_blocklist_extended.txt
https://gitlab.com/quidsup/notrack-blocklists/raw/master/notrack-malware.txt
https://v.firebog.net/hosts/Shalla-mal.txt
https://raw.githubusercontent.com/Spam404/lists/master/main-blacklist.txt
https://raw.githubusercontent.com/FadeMind/hosts.extras/master/add.Risk/hosts
https://urlhaus.abuse.ch/downloads/hostfile/
https://zerodot1.gitlab.io/CoinBlockerLists/hosts_browser
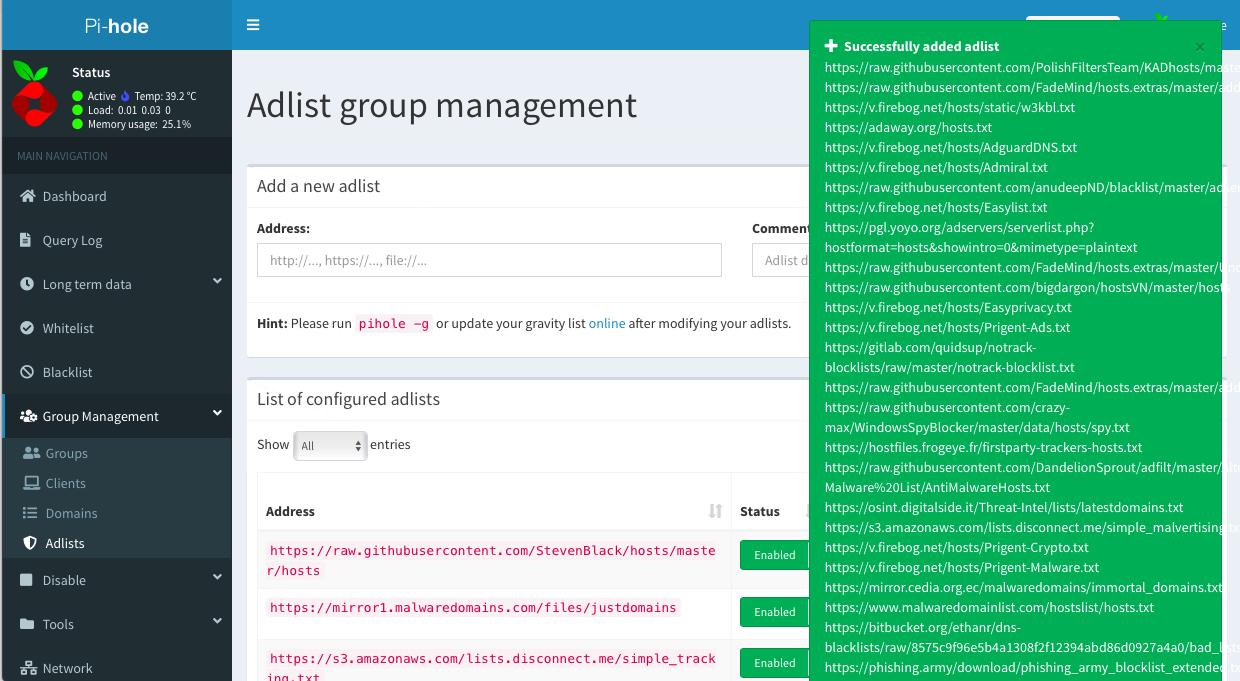
After finished add rules, you need to make it taking effect bypihole -g.
This command will pull all the files involved, and put them into /etc/pihole/,
to the end, it will report the results as below:
[✓] Storing downloaded domains in new gravity database
[✓] Building tree
[✓] Swapping databases
[i] Number of gravity domains: 432772 (320381 unique domains)
[i] Number of exact blacklisted domains: 0
[i] Number of regex blacklist filters: 1
[i] Number of exact whitelisted domains: 0
[i] Number of regex whitelist filters: 0
[✓] Flushing DNS cache
[✓] Cleaning up stray matter
[✓] DNS service is running
[✓] Pi-hole blocking is Enabled
NOTE: adding an already added list will abort the operation, so remove below to
files from the ticked list before adding to Adlists:
https://s3.amazonaws.com/lists.disconnect.me/simple_ad.txt
https://mirror1.malwaredomains.com/files/justdomains
Update:
This issue was fixed by this pull request made by DL6ER.
Another way to make new rules working is by using the web interface, in the side
panel, go to Tools >> Update Gravity, then click Update:
Update
Updating Pi-hole is much easier, another one command:
pihole -up
Pi-hole command can also be used for query an entry or add domain(s) to blacklist/whitelist:
pi@raspberrypi:~ $ pihole -q adslvfile.qq.com
Match found in https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts:
adslvfile.qq.com
Match found in https://adaway.org/hosts.txt:
adslvfile.qq.com
Match found in https://raw.githubusercontent.com/bigdargon/hostsVN/master/hosts:
adslvfile.qq.com
